Easy Methods to Learn Domain Authority Check
페이지 정보

본문
As I described final week, down on the very bottom of the display screen would be the options to display extra of the text that was cut off because it's method longer than will fit on the display screen, additionally to repeat your entire question outcomes to the system's clipboard. Steve: So we're going to likely learn by this time next week, we'll have feedback from our listeners who have used Rob's tool. Steve: Yes. Even without any decryption, what you get is a comprehensive dump of exactly who logs on exactly where. Oh, no. Okay, yes. Leo: Oh, no. I mean, it is perfectly potential, we don't know, that there's any person proper now running his old bitcoin mining apparatus, as a result of he does not have any use for that anymore, towards the entire vaults, and simply the first ones that come out are those he is going to make use of, proper, because they have bad passwords or no matter. Steve: Yeah, properly, I had actually old ones, too. Steve: Yes. Well, so I did a take a look at. A test case management instrument is a software application designed to help handle the creation, execution, and monitoring of test cases and related info. The corporate wants to ensure that the software is tailored to the French language, forex, tax regulations, and other particular requirements of France.
 Before diving into software options, it’s essential to know that there are manual methods accessible for converting JPG information to Word format. Your key phrases-the phrase combos and phrases that customers enter into Google-are a significant a part of your Google Ad Grant campaigns. In addition, PayPal was also slow to develop new features that would be helpful for eBay users. Domestic PayPal fees apply when the sender and receiver are registered with or recognized by PayPal as residents of the European Economic Area (EEA). While there isn't a silver bullet for bettering social indicators, there are numerous issues you can do to provide your webpage a boost. We know that 2’s complement of positive number gives a destructive quantity. Step 3 − If there may be an finish-round carry, it exhibits the result's optimistic and the final result's obtained by including the top-round carry to the intermediate end result. The token signature is the results of passing the header, payload, and a secret through a hash operate, acquiring a hard and fast worth.
Before diving into software options, it’s essential to know that there are manual methods accessible for converting JPG information to Word format. Your key phrases-the phrase combos and phrases that customers enter into Google-are a significant a part of your Google Ad Grant campaigns. In addition, PayPal was also slow to develop new features that would be helpful for eBay users. Domestic PayPal fees apply when the sender and receiver are registered with or recognized by PayPal as residents of the European Economic Area (EEA). While there isn't a silver bullet for bettering social indicators, there are numerous issues you can do to provide your webpage a boost. We know that 2’s complement of positive number gives a destructive quantity. Step 3 − If there may be an finish-round carry, it exhibits the result's optimistic and the final result's obtained by including the top-round carry to the intermediate end result. The token signature is the results of passing the header, payload, and a secret through a hash operate, acquiring a hard and fast worth.
 To allow your binary to run you'll be able to either use sbsign to signal your efi binary with the PK/KEK key or you possibly can go to the DB Options menu and merely choose the efi binary from the disk and have OVMF enroll the hash for you. Does it mean you possibly can, I imply, you continue to need to - a hash cannot be reversed, but you should use rainbow tables simply. For this objective, we can use the next codes. Altering the anchor textual content of a backlink can show challenging if your rapport with the linking web site isn’t robust. Backlink Watch is a dedicated webpage for checking backlinks of any given URL. Given the amount of effort that will generally be required - and we have now a bracing update on that coming up next - to brute drive the decryption of the encrypted data in even one LastPass vault, coupled with the fact that tens of hundreds of thousands of LastPass person vaults have been obtained en masse, the direct menace of decryption for a single individual, except immediately targeted, would appear to be very small.
To allow your binary to run you'll be able to either use sbsign to signal your efi binary with the PK/KEK key or you possibly can go to the DB Options menu and merely choose the efi binary from the disk and have OVMF enroll the hash for you. Does it mean you possibly can, I imply, you continue to need to - a hash cannot be reversed, but you should use rainbow tables simply. For this objective, we can use the next codes. Altering the anchor textual content of a backlink can show challenging if your rapport with the linking web site isn’t robust. Backlink Watch is a dedicated webpage for checking backlinks of any given URL. Given the amount of effort that will generally be required - and we have now a bracing update on that coming up next - to brute drive the decryption of the encrypted data in even one LastPass vault, coupled with the fact that tens of hundreds of thousands of LastPass person vaults have been obtained en masse, the direct menace of decryption for a single individual, except immediately targeted, would appear to be very small.
Otherwise, it requires brute power. 17.2 Neither occasion shall be liable to the other as a result of any delay or failure to carry out its obligations under this agreement because of a Force Majeure event. Fixed STRBEFORE and STRAFTER analysis to match languages if present and add the needle language to the consequence. This unfavourable impression can lead to guests leaving the site, growing the bounce fee and reducing the typical time spent on your webpage. Analyze your webpage's analytics information to establish pages with excessive bounce charges and low common time on site. Okay. So with the vault made accessible to the app, both by pasting it or convert jpg to ico file opening a file, specify an output filename to obtain the deobfuscated data and select the output format, both CSV or HTML. So set the filename, ending in either CSV or HTML as needed, and end by clicking "Analyze." The file will probably be written, after which the resulting file will likely be launched for display by whatever handler that your system has registered for handling that kind of file. Steve: And if you scroll horizontally all of the technique to the suitable of Rob's HTML output, there's also a final Touched area.
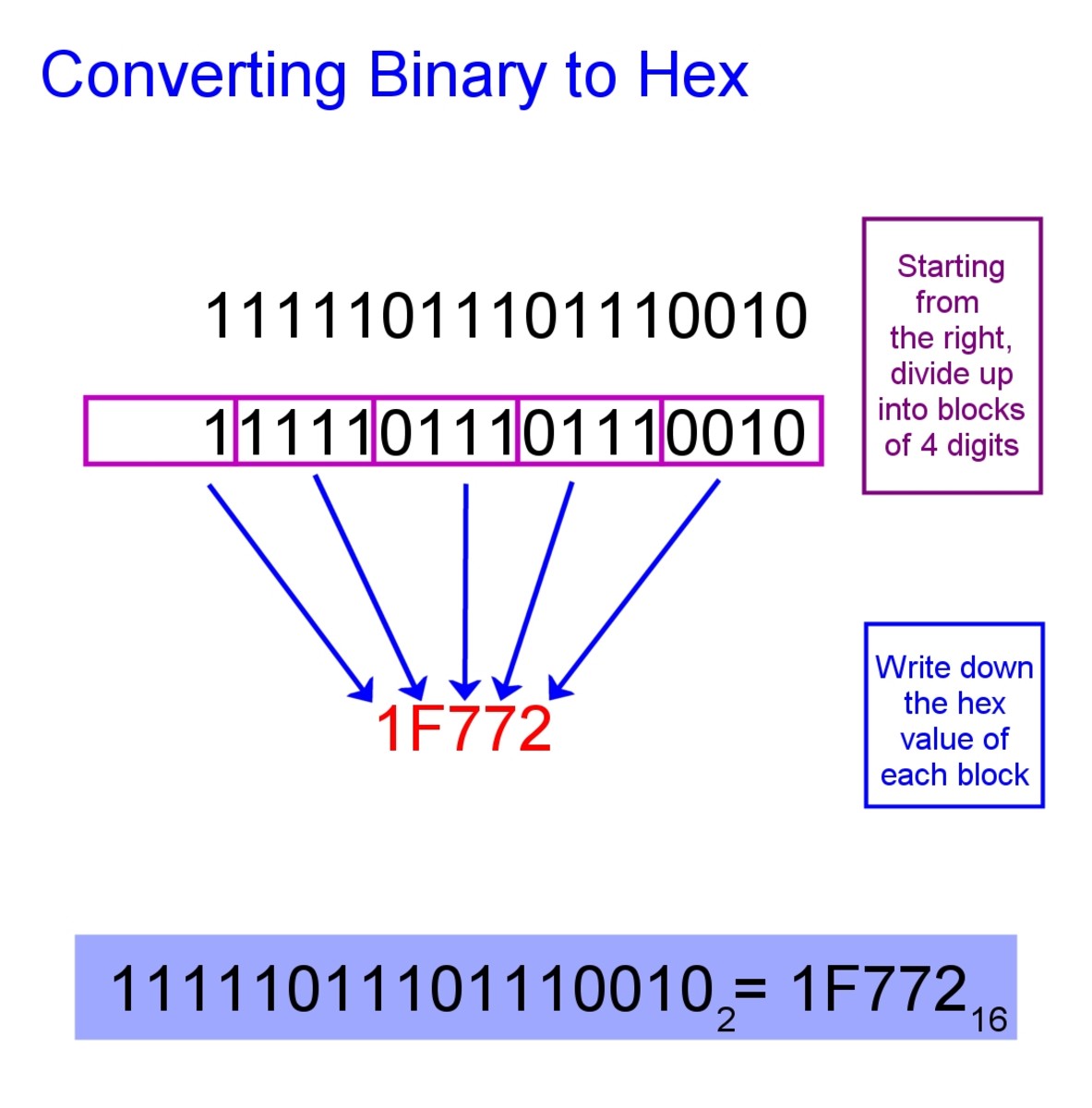
If you have any type of inquiries concerning where and ways to use how to convert hex to binary, you can call us at our own web-page.
- 이전글New Questions about Png To Ico File Answered And Why You should Read Every Word Of This Report 25.02.14
- 다음글Here is A fast Manner To resolve A problem with Seo Studio 25.02.14
댓글목록
등록된 댓글이 없습니다.

